Threat Watch
Instantly assess your cybersecurity health and uncover threats with actionable insights from Threat Watch.
Visit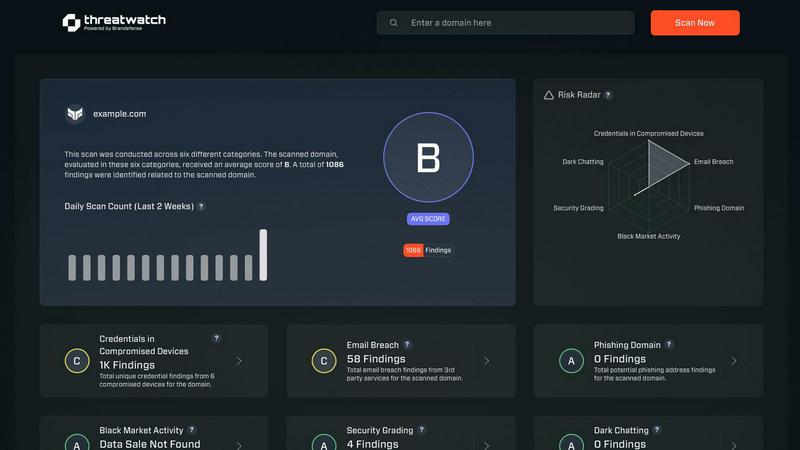
About Threat Watch
Threat Watch is a cutting-edge cybersecurity intelligence platform designed to safeguard organizations from the ever-evolving landscape of cyber threats. It meticulously assesses your organization's assets, vulnerabilities, and exposures, providing a comprehensive overview of your cyber health. By harnessing the power of real-time insights and automated assessments, Threat Watch enables organizations to swiftly identify, prioritize, and mitigate risks, enhancing overall security posture. Whether you are a small business or a large enterprise, Threat Watch is tailored for anyone seeking to bolster their cybersecurity defenses. Its user-friendly interface and robust analytics empower security teams to make informed decisions, ensuring that potential threats are neutralized before they can cause harm. Experience cybersecurity like never before and uncover your organization's cyber health in a flash with Threat Watch.
Features of Threat Watch
Real-Time Insights
Stay ahead of cyber threats with Threat Watch's real-time insights feature. This functionality provides continuous monitoring of your organization's assets and vulnerabilities, enabling you to receive immediate alerts about potential risks. With up-to-the-minute information, security teams can respond quickly and effectively, ensuring that your organization remains protected against emerging threats.
Automated Assessments
Efficiency meets effectiveness with Threat Watch's automated assessments. This feature conducts regular evaluations of your cybersecurity posture without requiring manual intervention. By automatically scanning for vulnerabilities and exposures, Threat Watch allows organizations to maintain a proactive security strategy, freeing up valuable resources and time for security teams to focus on critical issues.
Comprehensive Vulnerability Analysis
Threat Watch offers a thorough analysis of your organization's vulnerabilities across multiple categories. By evaluating credentials in compromised devices, breached accounts, phishing addresses, and dark web contents, this feature provides a holistic view of your security landscape. Identify weaknesses and take action before they can be exploited by malicious actors.
User-Friendly Dashboard
Navigate your cybersecurity landscape with ease using Threat Watch's intuitive dashboard. The user-friendly interface consolidates vital information, making it simple to interpret complex data. Whether you are reviewing security statuses or generating reports, the dashboard ensures that you have all the necessary insights at your fingertips, enhancing decision-making processes and response times.
Use Cases of Threat Watch
Small Business Cybersecurity
Small businesses often lack the resources to implement extensive cybersecurity measures. Threat Watch provides these organizations with essential insights into their security posture, enabling them to identify vulnerabilities and prioritize mitigation efforts. This ensures that even small teams can defend against cyber threats effectively.
Enterprise Risk Management
Large enterprises face a multitude of risks due to their complex infrastructures. Threat Watch assists in identifying and managing these risks by delivering real-time insights into potential vulnerabilities. With automated assessments, enterprises can streamline their risk management processes and enhance their overall security efficacy.
Incident Response Preparation
Having a robust incident response plan is crucial for organizations of all sizes. Threat Watch equips security teams with the necessary data to prepare for potential incidents. By continuously monitoring assets and vulnerabilities, teams can develop response strategies and ensure that they are ready to act swiftly in the event of a cyber incident.
Cyber Health Assessment
Regular assessments of your cyber health are vital for maintaining security. Threat Watch provides organizations with comprehensive evaluations of their cybersecurity status. By uncovering weaknesses and identifying areas for improvement, organizations can proactively strengthen their defenses against cyber threats.
Frequently Asked Questions
What types of organizations can benefit from Threat Watch?
Threat Watch is designed for organizations of all sizes, from small businesses to large enterprises. Its comprehensive features cater to various industries, making it an essential tool for anyone looking to enhance their cybersecurity posture.
How does Threat Watch ensure real-time monitoring?
Threat Watch employs advanced algorithms and continuous scanning processes to provide real-time monitoring of your organization's assets and vulnerabilities. This ensures that you receive immediate alerts and insights on emerging threats.
Is Threat Watch easy to integrate with existing systems?
Yes, Threat Watch is built with compatibility in mind. It can seamlessly integrate with your existing security systems and workflows, ensuring a smooth transition and minimal disruption to your operations.
Can I customize the assessments conducted by Threat Watch?
Absolutely! Threat Watch offers customizable assessment options to meet your organization's specific needs and requirements. This flexibility allows you to focus on the vulnerabilities and risks most relevant to your operations.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
AILeadz
Revolutionize your sales strategy with AILeadz, the ultimate tool for finding and connecting with your ideal customers.
aVenture
aVenture is your AI-powered research hub for uncovering startup insights, tracking investments, and analyzing competi...